File Checksum Calculator
| Infocard
| ||||||||||||||||
| ||||||||||||||||
Verify cryptographic hashes in MD5 and SHA-1.
|
| 2.22 Mb |
Contents
Description by the Publisher
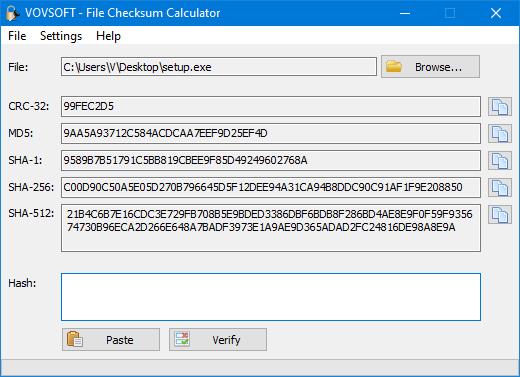
A standalone utility that generates and verifies cryptographic hashes in MD5, SHA-1 and SHA-256. Cryptographic hash functions are commonly used to guard against malicious changes to protected data in a wide variety of software, Internet, and security applications, including digital signatures and other forms of authentication. Two of the most common cryptographic hash functions are the Secure Hash Algorithm (SHA) and Message Digest Algorithm-5 (MD5). Checksum utilities are used to verify the integrity of generated hashes. There are two basic types, those that calculate checksum values and those that also validate them by checking them against a list of values for the protected data, which is the only way it can be done.
Limitations in the Downloadable Version
No limitations
Product Identity
Unique Product ID: PID-92004EB92D71
Unique Publisher ID: BID-D0006972CF2C
[File Checksum Calculator PAD XML File]